Cyber attacks are on the rise. Many organisations are tightening their belts at the moment, looking for ways to save money. But caution those that cut from their information security budget - this is an area where organisations will never see return on investment, but they could certainly see a very large downside if they fail to prepare.
Take heed from those organisations who didn't prepare adequately:
- Jaguar Land Rover
In August 2025 a large-scale ransomware attack shut down IT operations across all JLR areas, including operations, payments, part tracking etc. As a result manufacturing has shut down at many sites, some analysts estimate losses from the attack will reach $2 billion USD ($2,000,000,000). The problem threatens to bankrupt smaller firms across the UK automotive supply chain, which would result in thousands of job losses. As of October 2025 the issue is still not resolved.
- Marks & Spencer
Around Easter 2025 a hacking group gained access to M&S systems by exploiting a trusted third party partner - Tata Consulting Services (TCS). Once inside they wreaked havoc by deploying a ransomware attack which disrupted online sales operations for over four months. The cost of the attack was estimated around $400M USD through lost sales.
- British Airways
In 2018 a hacking group was able to breach BA’s systems and obtain personal & financial details of customers via their website & mobile app. As a result BA were fined £20M (around $25,000,000 USD) by the information commissioners office.
- 23andMe
Hackers reused credentials that had been exposed in old attacks to gain access to end user accounts at 23andMe. They took advantage by stealing information about DNA relatives, family trees and ancestry information. Although no financial or genetic data was stolen, the reputational damage was immense. The company was fined $3M USD by the information commissioners office. They filed for bankruptcy two years later.
- Hackney Borough Council
In 2020 hackers deployed a ransomware attack on the council’s IT systems which disrupted all areas of council management, and stole sensitive personal data of some 280,000 individuals (including financial records, criminal records, religion, health and sexual orientation data). The ransomware attack caused significant disruption to local services (bin collections, council tax collection, benefits payments), has led to irreversible data loss and as of 2025 some council operations are still impacted.
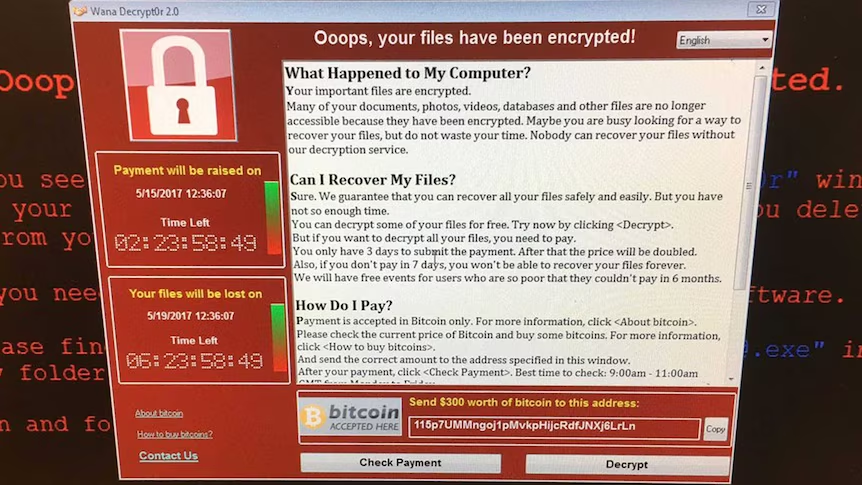
- The NHS
The National Health Service in the United Kingdom has been subject to many cyber attacks, most notably ransomware attacks in 2017, 2022 and 2024 which severely disrupted healthcare operations leading to real world outcomes like cancellation of appointments, surgical operations and tangible financial losses. Hackers stole patient medical records, contact details and in some cases even details about how to enter homes of vulnerable patients. Tangible costs in cyber attacks to the NHS likely exceed $140M USD, and many patients suffered in the attack indirectly through healthcare outcomes.