If your application container crashed at 3am, but the pod was automatically restarted and nobody saw, did the crash even happen in the first place?
Your site reliability team would certainly say so, and they would like to know about it so that they can resolve the issue. Your adversaries would like to know too, in case they can exploit the problem.
With the 2099 Group blueprint we can get your SoC team up and running on Google Chronicle in no time at all. If you don’t have a SoC team and want to opt for a managed service, we can work with a variety of partners and SIEM engines. Our main partner offers services running on Google SecOps (Chronicle) and can offer 24x7 vigilance based out of their systems operations center in Leeds, UK.
We will work together with your development team, your SoC team (or SoC provider) and SRE teams to help deliver any custom log ingestion or detection rules that you would like, to give your team assurances that in your environment no trees will fall unheard.


Most tech companies will start with human monitoring. If something goes wrong then call an engineer out, get them to fish around in the logs for something relevant.
This will work up to a point but there are a lot of flaws in this strategy. For starters, most humans will fail to spot patterns in log files larger than a few hundred lines. After that, it all starts to look like white noise.
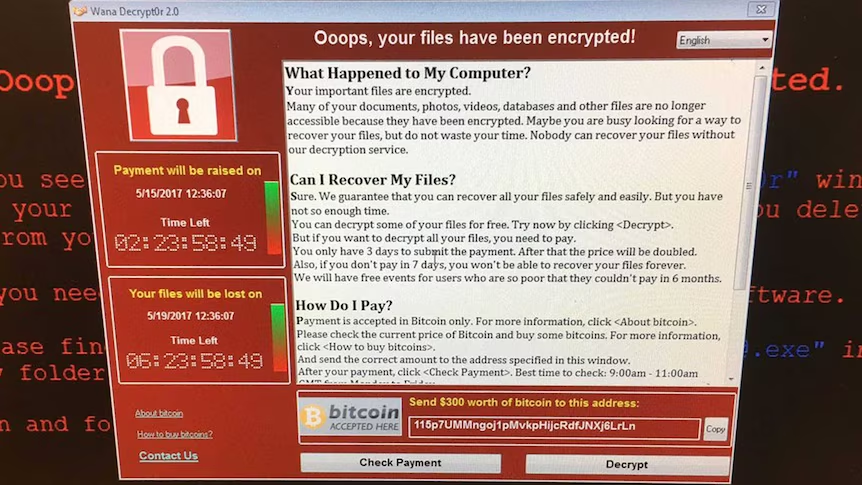
More serious than that, human log review is normally reactive and not pro-active. You will only find the problem if you already know that one exists. And if a problem occurred that you weren’t looking for? Like an unauthorised threat actor gaining access to your systems?
Well, if you weren’t looking at the logs you’ll never know...

Launched in 2023 as Chronicle, Google SecOps has quickly risen to become one of the top tools for security & incident event monitoring (SIEM) in the security and SRE space. Rather than leaving event schema up to the end users, it has a fixed event schema (known as UDM), and ingest pipelines pre-defined for most common log sources. Chronicle is great at correlating events from different log sources together, allowing you to build up a picture of what has happened in any given incident.
The search engine allows you to query through terabytes of log data instantly without having to do any sort of index management, using a very simple SQL-like search syntax. Chronicle comes with hundreds of detection rules built-in for picking up commonly encountered security issues and attack threat vectors such as repeated failed logins on various systems, port probing, superman attacks and more. The template rules allow you to get up and running without spending months writing rules for common attack scenarios. You can also write your own detection rules with the YARA-L language, and make custom dashboards for security and reliability monitoring.
Deploying a SIEM database can seem like a daunting task, but we have experts available and connections in the industry to help you succeed. Let us design your SIEM & SoC for success.